| 2022-12-29T11:58:57.907786499Z | stdout | Thu Dec 29 12:58:57 2022 SIGTERM[soft,auth-failure] received, process exiting |
| 2022-12-29T11:58:57.907646371Z | stdout | Thu Dec 29 12:58:57 2022 AUTH: Received control message: AUTH_FAILED |
| 2022-12-29T11:58:57.872833146Z | stdout | Thu Dec 29 12:58:57 2022 SENT CONTROL [it-mil-v082.prod.surfshark.com]: 'PUSH_REQUEST' (status=1) |
| 2022-12-29T11:58:52.791507264Z | stdout | Thu Dec 29 12:58:52 2022 SENT CONTROL [it-mil-v082.prod.surfshark.com]: 'PUSH_REQUEST' (status=1) |
| 2022-12-29T11:58:51.731817503Z | stdout | Thu Dec 29 12:58:51 2022 [it-mil-v082.prod.surfshark.com] Peer Connection Initiated with [AF_INET]178.249.211.140:1443 |
| 2022-12-29T11:58:51.731781326Z | stdout | Thu Dec 29 12:58:51 2022 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA |
| 2022-12-29T11:58:51.731741337Z | stdout | Thu Dec 29 12:58:51 2022 WARNING: 'auth' is used inconsistently, local='auth SHA512', remote='auth [null-digest]' |
| 2022-12-29T11:58:51.731682756Z | stdout | Thu Dec 29 12:58:51 2022 WARNING: 'cipher' is used inconsistently, local='cipher AES-256-CBC', remote='cipher AES-256-GCM' |
| 2022-12-29T11:58:51.731533774Z | stdout | Thu Dec 29 12:58:51 2022 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1635', remote='link-mtu 1583' |
| 2022-12-29T11:58:51.690621338Z | stdout | Thu Dec 29 12:58:51 2022 VERIFY OK: depth=0, CN=it-mil-v082.prod.surfshark.com |
| 2022-12-29T11:58:51.690592357Z | stdout | Thu Dec 29 12:58:51 2022 VERIFY EKU OK |
| 2022-12-29T11:58:51.690551313Z | stdout | Thu Dec 29 12:58:51 2022 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication |
| 2022-12-29T11:58:51.690503413Z | stdout | Thu Dec 29 12:58:51 2022 Validating certificate extended key usage |
| 2022-12-29T11:58:51.690461357Z | stdout | Thu Dec 29 12:58:51 2022 VERIFY KU OK |
| 2022-12-29T11:58:51.690073132Z | stdout | Thu Dec 29 12:58:51 2022 VERIFY OK: depth=1, C=VG, O=Surfshark, CN=Surfshark Intermediate CA |
| 2022-12-29T11:58:51.689697544Z | stdout | Thu Dec 29 12:58:51 2022 VERIFY OK: depth=2, C=VG, O=Surfshark, CN=Surfshark Root CA |
| 2022-12-29T11:58:51.536599588Z | stdout | Thu Dec 29 12:58:51 2022 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this |
| 2022-12-29T11:58:51.536411918Z | stdout | Thu Dec 29 12:58:51 2022 TLS: Initial packet from [AF_INET]178.249.211.140:1443, sid=b86f95fb bb6c81ab |
| 2022-12-29T11:58:51.518396624Z | stdout | Thu Dec 29 12:58:51 2022 TCP_CLIENT link remote: [AF_INET]178.249.211.140:1443 |
| 2022-12-29T11:58:51.518360678Z | stdout | Thu Dec 29 12:58:51 2022 TCP_CLIENT link local: (not bound) |
| 2022-12-29T11:58:51.518211407Z | stdout | Thu Dec 29 12:58:51 2022 TCP connection established with [AF_INET]178.249.211.140:1443 |
| 2022-12-29T11:58:50.518004607Z | stdout | Thu Dec 29 12:58:50 2022 Attempting to establish TCP connection with [AF_INET]178.249.211.140:1443 [nonblock] |
| 2022-12-29T11:58:50.517968660Z | stdout | Thu Dec 29 12:58:50 2022 Socket Buffers: R=[87380->87380] S=[16384->16384] |
| 2022-12-29T11:58:50.517911212Z | stdout | Thu Dec 29 12:58:50 2022 TCP/UDP: Preserving recently used remote address: [AF_INET]178.249.211.140:1443 |
| 2022-12-29T11:58:50.517858258Z | stdout | Thu Dec 29 12:58:50 2022 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication |
| 2022-12-29T11:58:50.517734510Z | stdout | Thu Dec 29 12:58:50 2022 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication |
| 2022-12-29T11:58:50.479958060Z | stdout | Thu Dec 29 12:58:50 2022 NOTE: --fast-io is disabled since we are not using UDP |
| 2022-12-29T11:58:50.479919354Z | stdout | Thu Dec 29 12:58:50 2022 WARNING: --ping should normally be used with --ping-restart or --ping-exit |
| 2022-12-29T11:58:50.479882070Z | stdout | Thu Dec 29 12:58:50 2022 library versions: OpenSSL 1.1.1g 21 Apr 2020, LZO 2.10 |
| 2022-12-29T11:58:50.479832148Z | stdout | Thu Dec 29 12:58:50 2022 OpenVPN 2.4.9 x86_64-alpine-linux-musl [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Apr 20 2020 |
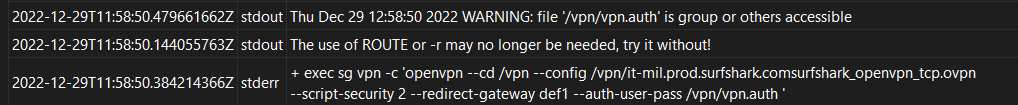
| 2022-12-29T11:58:50.479661662Z | stdout | Thu Dec 29 12:58:50 2022 WARNING: file '/vpn/vpn.auth' is group or others accessible |
| 2022-12-29T11:58:50.144055763Z | stdout | The use of ROUTE or -r may no longer be needed, try it without! |
| 2022-12-29T11:58:50.384214366Z | stderr | + exec sg vpn -c 'openvpn --cd /vpn --config /vpn/it-mil.prod.surfshark.comsurfshark_openvpn_tcp.ovpn --script-security 2 --redirect-gateway def1 --auth-user-pass /vpn/vpn.auth ' |
| 2022-12-29T11:58:50.384183851Z | stderr | Perhaps ip6tables or your kernel needs to be upgraded. |
| 2022-12-29T11:58:50.384145962Z | stderr | ip6tables v1.8.4 (legacy): can't initialize ip6tables table `nat': Table does not exist (do you need to insmod?) |
| 2022-12-29T11:58:50.384066486Z | stderr | Perhaps ip6tables or your kernel needs to be upgraded. |
| 2022-12-29T11:58:49.965881578Z | stderr | ip6tables v1.8.4 (legacy): can't initialize ip6tables table `nat': Table does not exist (do you need to insmod?) |
| 2022-12-29T11:58:49.353106183Z | stdout | The use of ROUTE or -r may no longer be needed, try it without! |